Redefining Human-Computer Interaction with Ambient Computing
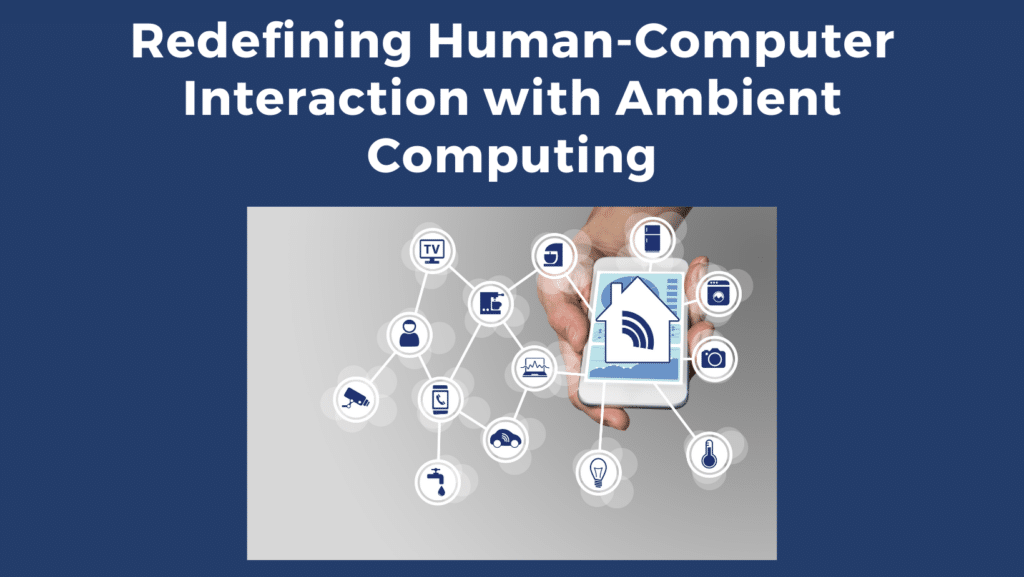
How will Ambient Computing change our future? First, you need to know what Ambient Intelligence is. Ambient intelligence, or AmI, is the capacity of technology to make judgments and act on our behalf while taking into account our preferences based on the data made accessible to it from all the linked sensors and devices surrounding […]
IoT AT WORK: CYBER SECURE YOUR SMART BUSINESS

Businesses are using internet-connected gadgets to improve productivity, cut costs, save energy, and reap a variety of other advantages. All of these advantages, meanwhile, come with security and privacy dangers. Keep in mind that every new device you use that is connected to the internet gives a cybercriminal another entrance point. The National Cybersecurity Alliance […]
Microsoft Cloud for Sustainability

It’s time to invest in sustainability in everything we do, and Microsoft Cloud for Sustainability can help. Wherever you are on your path to net zero, Microsoft Cloud for Sustainability enables you to amplify progress and transform your business through environmental, social, and governance (ESG) capabilities. Microsoft Cloud for Sustainability can: Read more about how […]
What is cloud computing?
Looking to migrate your business to the cloud but feeling a bit apprehensive? We will help you make the decision by providing you with everything you need to know about the cloud. To put it simply, cloud computing is the transmission of computing services over the Internet (“the cloud”) in order to provide speedier innovation, […]
LTS Announcement: Tech Gallery is Open for Business!

Things are really moving along with our new location, Tech Gallery. Signage is up, the store has a few display desktops available for guests to peruse, and we have folks walking in the door to drop off their devices for repair services. We are still working on getting in more inventory, as well as display […]
Social Engineering Trends in Cybersecurity
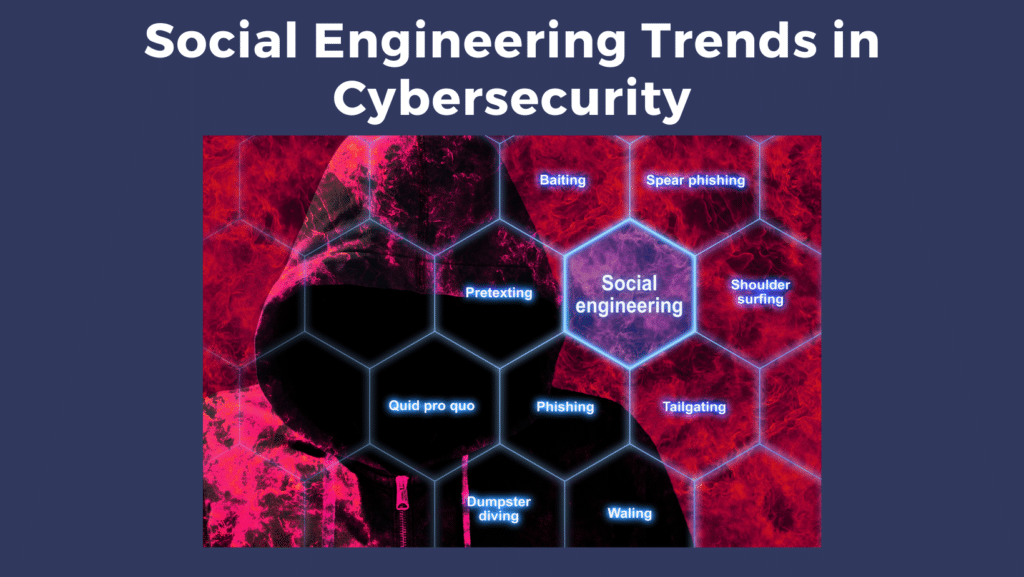
“Cybercriminals are developing and enhancing their attacks at an upsetting rate, exploiting the uncertainty and fear caused by shaky economic and social circumstances.” -Jurgen Stock, Interpol Secretary-General Cyberthreats continue to rise and cybercriminals are finding new ways to attack every day. At the height of the COVID-19 pandemic in 2020, phishing attacks increased by 220 […]
Hurricane Season – Is your business prepared

Hurricanes, and other natural disasters, can cause extensive damage. We are now hearing on the news that we need to have our Hurricane Kits ready: Weather radio, extra batteries, tarps, granola bars, bottled water, extra medication, pet care needs, emergency phone numbers, shelter sites… the list is long! But what about your business operations […]
Cybersecurity Insurance: What It Is, Which Businesses Need It

According to a recent report, US businesses are more likely to pay a ransom to get their data recovered after a cyber assault. Currently, 71% of those targeted have paid up. Cyber liability insurance can shield your company from the costs of a data breach — and it also covers hazards you may not have […]
Orlando Emerges as the Center of the Metaverse

Have you heard the buzz about Orlando’s new slogan,”Unbelievably Real?” Visit Orlando and the Orlando Economic Partnership have combined their brain trusts to create “Unbelievably Real,” a new branding campaign for the region. Watch the video below to learn more: Next-generation gaming, entertainment, artificial intelligence, AR/VR, IoT, and simulation training enterprises are a huge part […]
7 Tips for Training Employees About Cybersecurity Awareness

How long has it been since you’ve trained your employees on cybersecurity? The best way to reduce the danger of a network attack is to strengthen your first line of protection, which includes cybersecurity awareness training for your personnel. The National Institute of Standards and Technology, states that organizations “should assume that malicious parties will […]
